Latest Version
1.0.5
November 15, 2024
Jenny Pham
iPhone
iOS
628 MB
0
Free
Report a Problem
More About ERROR143
This application is about a hacking competition between two rivals. The user has just been bested by their rival and they are not going to let it slide. They decide to hack into their rival's database and leave a message to prove their superiority. However, their rival has also hacked them back. This sets the stage for a back and forth hacking battle between the two rivals.
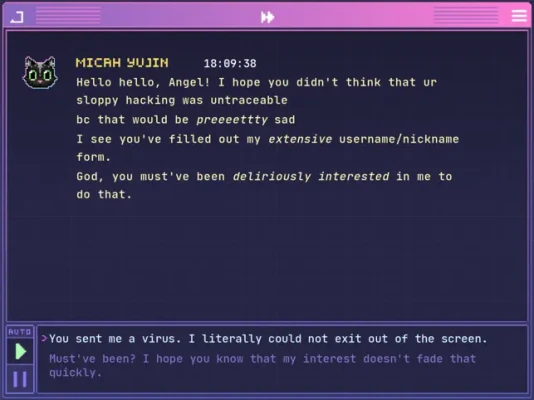
The user is determined to come out on top and show their rival who is the better hacker. They use their skills to access their rival's database and leave a message, possibly taunting or gloating about their victory. This action not only proves their superiority, but also serves as a form of revenge for being bested in the competition.
But the user's rival is not one to back down easily. They have also hacked into the user's database and left a message, possibly challenging them to continue the hacking battle. This adds an element of competition and excitement to the application, as the user now has to strategize and come up with a plan to outsmart their rival's hacking skills.
The application highlights the competitive nature of hacking and the determination of individuals to come out on top. It also showcases the back and forth nature of hacking battles, where one move can lead to a counter move from the other side. This creates a thrilling and intense atmosphere for the user, as they try to outsmart their rival and prove their superiority in the world of hacking.
In conclusion, this application is about a hacking competition between two rivals, where the user is determined to prove their superiority after being bested by their rival. The back and forth hacking battle between the two rivals adds an element of competition and excitement to the application, making it a thrilling experience for the user. It also highlights the competitive nature of hacking and the determination of individuals to come out on top.
Rate the App
User Reviews
Popular Apps